
Passwords are one of the easiest targets for cybercriminals and if they aren’t stored properly, they can be cracked in no time. Hashing is a way to protect passwords by turning them into an irreversible string of characters so even if a database is breached attackers can’t just see them. But not all hashing methods are the same, some are much easier to crack than others.
The Siker Password Hashing Challenge was all about showing the difference between weak and strong password security and why using unique and complex passwords is so important. There were three challenges each one getting trickier as we went along.
Challenge Breakdown & Solutions
The best and fastest way to solve these challenges was to use password cracking tools such as Hashcat, John the Ripper, or online hash databases like CrackStation. Each challenge required a different approach. Some could be cracked instantly with online tools, while others needed a bit of extra thinking. Below is how each challenge could be solved.
Step 1 – The MD5 Hash
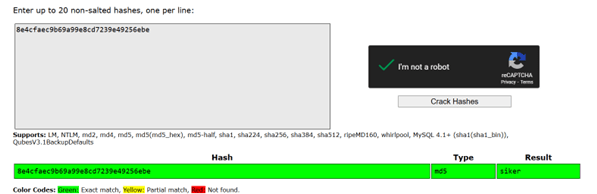
The first challenge was simple just to get everyone started. We gave participants an MD5 hash of the password ‘siker’ and told them exactly which hash algorithm was used.
MD5 is outdated and not secure at all for passwords. It can be cracked almost instantly using online tools. This challenge showed how weak MD5 is and why it shouldn’t be used anymore for protecting passwords.
https://crackstation.net/
Step 2 – Spot the Weak Link
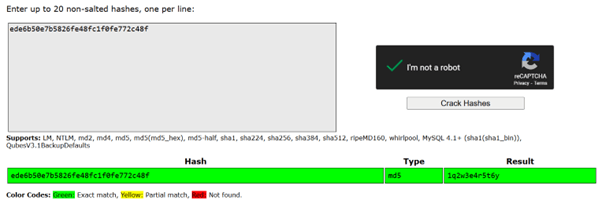
Next, we made it a bit harder. We gave a list of salted MD5 hashes but hid one unsalted hash in the middle of them. The challenge was to spot and crack the correct one.
The real password was ‘1q2w3e4r5t6y’ which might look more complex at first glance but it’s actually one of the most common passwords out there. Even though it’s longer, it still appears in many password breach lists which means modern cracking tools can guess it in seconds. The lesson here was that password length alone isn’t enough if the password isn’t unique.
https://crackstation.net/
Step 3 – A Layered Challenge
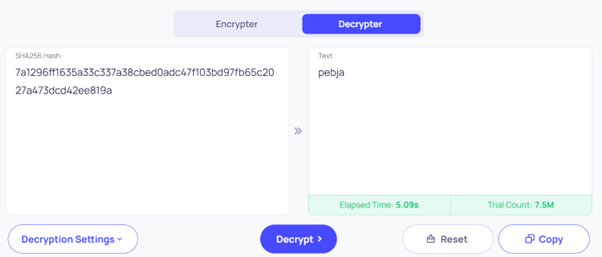
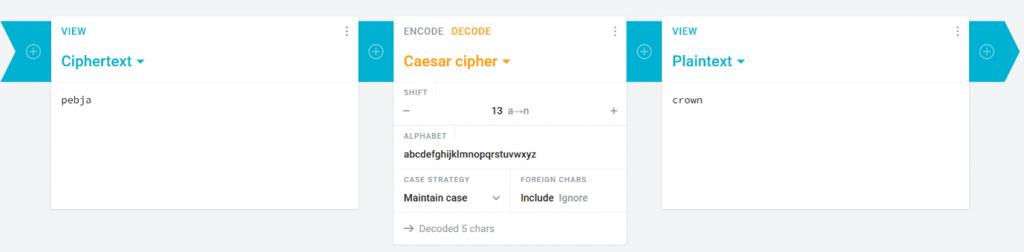
For the final step we wanted to make things more interesting and fun. Instead of just hashing the password, we first ran it through a Caesar cipher (ROT13) before hashing it with SHA-256.
The actual password was ‘crown’ but if you had tried cracking the SHA-256 hash directly it would have looked like complete nonsense. With a little bit of time and research, you would have realised that we had used the most common Caesar cipher shift (ROT13).
Once you had realised it was a Caesar cipher, you could have worked out the shift manually, but you also could have made it easier by using an online decoder. For example, the one in the image below where you put in the ciphertext and kept increasing the shift number until you saw a word in plaintext that made sense.
For those who looked closely, we even left a little hint on LinkedIn: a tiny Caesar salad in the top left corner of a post.
https://10015.io/tools/sha256-encrypt-decrypt
https://cryptii.com/pipes/caesar-cipher
A huge congratulations to our winners:
🥇 Cameron P – Raspberry Pi Kit
🥇 Tzortzino M – Razer Mechanical Keyboard
🥇 Wojciech B – 3 Month TryHackMe Membership
🥇 Derry M – 3 Month TryHackMe Membership
🥇 Eljay L – 3 Month TryHackMe Membership
Massive thanks to everyone who took part. This challenge was all about showing why password security matters and hopefully it was a fun way to learn. The biggest takeaway: Use strong unique passwords and avoid weak outdated hashing methods
Follow us on LinkedIn to stay updated on all our work, updates & future events.
Challenge creator/author: Alhasan Jouhoune
